Leader in cyber security solutions
Check Point
Check Point Software Technologies is a leading provider of cyber security solutions to corporate enterprises and governments globally. Its solutions protect customers from 5th-generation cyber-attacks with an industry leading catch rate of malware, ransomware and other targeted attacks.
Check Point offers a multilevel security architecture with our new Gen V advanced threat prevention that protects all networks, cloud and mobile operations of a business against all known attacks combined with the industry’s most comprehensive and intuitive single point of control management system. Check Point protects over 100,000 organizations of all sizes.

PRODUCTS

Security Architecture
Security Architecture: Step up to Gen V of cyber security

CloudGuard - Solutions for cloud
Check Point cloud security family
Solutions for mobile
SandBlast Mobile: Check Point mobile solutions


Check Point Infinity – Step Up to Gen V of Cyber Security
Today we are in the midst ofthe 5th generation of cyberattacks, battling the most advanced and impactful large scale, multi-vector mega attacks. Previous generations of cyber security are simply not enough. Time to step up to Gen V of cyber security with Check Point Infinity Architecture.
Gen V of Cyber Security
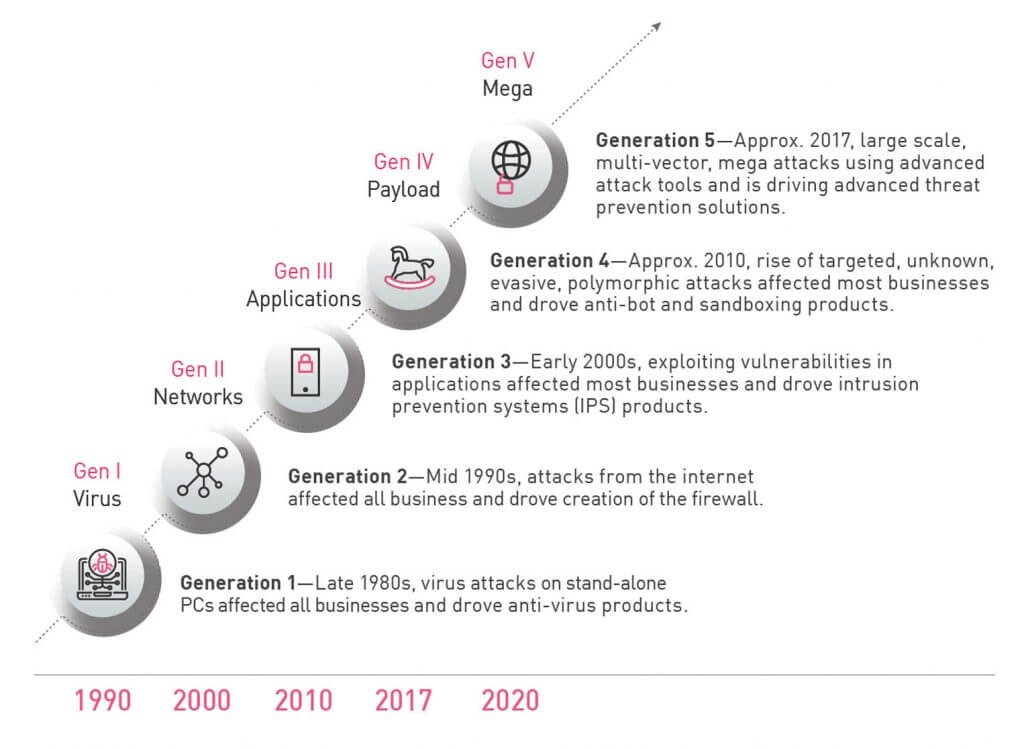
In 2017 we saw unprecedented cyber-attacks carried out as large-scale, multi-vector mega attacks that inflicted major damage on businesses and their reputation. Looking back, it is easy to identify the different generations of both attacks and security solutions. Today’s attacks are the most advanced and impactful we have ever seen, as we find ourselves in the midst of the 5th generation of cyber-attacks. However, the security deployed by most businesses is generationally lagging behind and incapable of protecting against such attacks. Specifically, while we are facing the 5th generation of attacks, most businesses only have 2nd or 3rd generation security.
Check Point Infinity Architecture
Check Point Infinity is the only fully consolidated cyber security architecture that protects against Gen V mega cyber-attacks across all networks, endpoint, cloud and mobile.
The architecture is designed to resolve the complexities of growing connectivity and inefficient security. It provides complete threat prevention which seals security gaps, enables automatic, immediate threat intelligence sharing across all security environments, and a unified security management for an utmost efficient security operation.
Check Point CloudGuard

The CloudGuard cloud security family provides consistent and comprehensive cloud security for virtualized datacenters to SDN, IaaS and SaaS applications, including the emerging threat of account takeover. The CloudGuard portfolio includes CloudGuard SaaS and CloudGuard IaaS, and seamlessly integrates with the largest number of cloud platforms and cloud-based applications, giving customers the freedom to choose the cloud solution that best aligns with their goals without sacrificing security.
CloudGuard SaaS is an industry-first security solution designed to provide advanced security and threat prevention for software-as-a-service (SaaS) applications, and uses a patent-pending technology that prevents account takeover as well as hacking of SaaS applications.
CloudGuard IaaS provides advanced Gen V threat prevention for all leading public and private cloud platforms including: Amazon Web Services, Google Cloud Platform, Microsoft Azure, Cisco ACI, OpenStack, VMware NSX, VMware Cloud on AWS, VMware ESX, Alibaba Cloud, KVM, Hyper-V and more.
How We Can Help?
SaaS Security
SaaS applications deliver many benefits to businesses of all sizes, but also expose them to risks from advanced threats largely due to unauthorized access to corporate SaaS accounts.
CloudGuard SaaS
CloudGuard SaaS provides complete protections against even the most sophisticated malware and zero-day threats while easily preventing account breaches. With Check Point CloudGuard, SaaS security is just one click away.
Learn more about CloudGuard SaaS

IaaS Public Cloud Security

Moving compute resources and data to public clouds means security responsibilities become shared between you and your cloud provider. Businesses want the ability to control their own data and keep it private as well as protect cloud assets, all while maintaining compliance with regulatory mandates.
CloudGuard IaaS Public Cloud Security
Check Point CloudGuard delivers automated and elastic security to keep assets and data protected while staying aligned to the dynamic needs of public and hybrid cloud environments.
Learn more about CloudGuard IaaS Public Cloud Security
Private Cloud Security
Network virtualization has created a shift in traffic behavior with more traffic going East-West in the data center, allowing threats to travel unimpeded once inside the data center and spread laterally.
Check Point CloudGuard IaaS Private Cloud Security
Check Point CloudGuard delivers dynamic security within virtual datacenters to prevent the lateral spread of threats while consolidating visibility and management across physical and virtual networks.
Learn more about CloudGuard SaaS
Mobile Security
Today every business is a mobile business, with requirements to safeguard business data, provide secure mobile access to business documents and keep mobile devices safe from threats.
Check Point enterprise mobile security solutions provide the widest range of products to help you secure your mobile world.

Mobility increases risk of breach
How Check Point Can Help?
SandBlast Mobile
Using smartphones and tablets to access critical business information on the go has many benefits, but it can also expose sensitive data to risk.
Check Point SandBlast Mobile protects iOS and Android devices from advanced mobile threats, ensuring you can deploy and defend devices with confidence.
Learn more about Sandblast mobile


Check Point Capsule
Mobile security and complexity don’t have to go hand in hand.
Check Point Capsule is one seamless solution that addresses all your mobile security needs. Capsule provides a secure business environment for mobile device use and protects business documents wherever they go.
Learn more about Check Point Capsule
Endpoint Security
Mobile endpoints are a frequent source of data loss and attacks.
Check Point Endpoint Security is a single agent providing data security, network security, threat prevention and a remote access VPN for complete Windows and Mac OS X security. As an integrated suite, Endpoint Security provides simple, unified management and policy enforcement.
Learn more about Endpoint Security